Secure E-Invoice Transmission: A Technical Guide for IT and Security Teams
Estimated reading time: 12 minutes
Key takeaways
- Secure e-invoice transmission protects confidentiality, integrity, authenticity, and non-repudiation through encryption and controlled access.
- Transport encryption (TLS) is the baseline; payload-level encryption adds protection for sensitive invoice data in multi-party chains.
- Digital signatures and certificates ensure authenticity and prevent tampering, creating evidence trails for tax compliance and audits.
- Modern platforms combine encrypted delivery with automated validation, RBAC, and audit-proof archiving to reduce fraud and operational risk.
- EU-compliant structured formats (XRechnung, ZUGFeRD, UBL) work best when combined with end-to-end security controls.
Table of contents
- Title
- Key takeaways
- What Defines a Secure E-Invoice
- Core Security Objectives for Encrypted Invoice Delivery
- Technical Transmission Methods and Protocols
- Encryption Layers in Invoice Transmission
- Security Features in Modern E-Invoicing Platforms
- Typical Secure Delivery Flows
- Benefits of Secure and Encrypted E-Invoices
- Practical Design Guidelines for IT and Security Teams
- FAQ
What Defines a Secure E-Invoice
A secure e-invoice is an electronic invoice generated, transmitted, received, and stored in a way that prevents unauthorized access or modification while providing a verifiable audit trail. In practice, this means the invoice data stays confidential during transmission, arrives unchanged, comes from a verified sender, and leaves evidence that can't be denied later.
Technical controls typically include:
- Encryption during transit (TLS/HTTPS) and optionally at the payload level.
- Digital signatures or seals to prove origin and detect changes.
- Aligned access control policies in sender and recipient systems.
- Automated validation against POs and master data to catch fraud or duplicates before payment.
In German, a "sichere E-Rechnung" requires confidentiality (Vertraulichkeit), immutability (Unveränderbarkeit), proof of origin (Herkunftsnachweis), and traceability (Nachvollziehbarkeit) according to legal and tax rules. Encrypted transport channels, unique identifiers, detailed logging, and audit-proof archiving are common building blocks.
Operational caution: invoicing spans ERP, procurement, payment gateways, and external networks—security must be end-to-end. A single weak link (an unencrypted file share, a misconfigured S3 bucket) can nullify strong TLS or signing controls.
Core Security Objectives for Encrypted Invoice Delivery
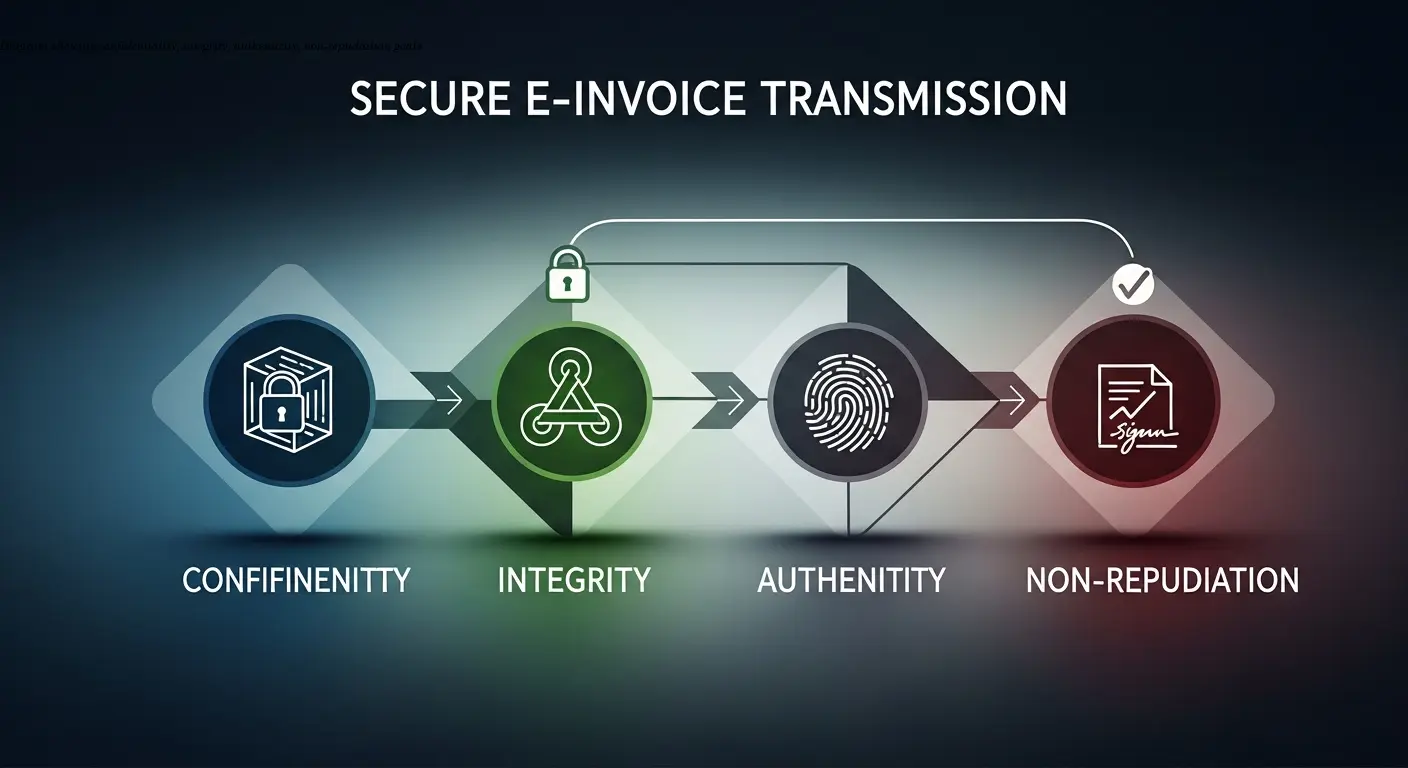
Secure e-invoice transmission focuses on four protection goals that directly prevent real-world attacks like invoice fraud and payment diversion:
Confidentiality
Ensures only authorized parties can view invoice data via transport encryption (TLS) and strict access control. For high-risk scenarios, payload-level encryption prevents intermediaries from reading invoice content.
Integrity
Means invoice content cannot be altered without detection. Checksums, digital signatures, and tamper-evident logs ensure the received invoice matches what the supplier sent—critical for tax and audit requirements.
Authenticity
Proves who sent the invoice via certificates, signatures, or strong credentials, often combined with supplier validation and unique invoice identifiers to prevent spoofing.
Non-repudiation and auditability
Creates evidence of when and by whom an invoice was issued and received using digital signatures, timestamps, and logs. This is essential for dispute resolution and regulatory compliance.
Lesson learned: Adding signatures after go-live with optional fields leads to missing signatures and audit failures—design these controls into the process from the start.
Technical Transmission Methods and Protocols
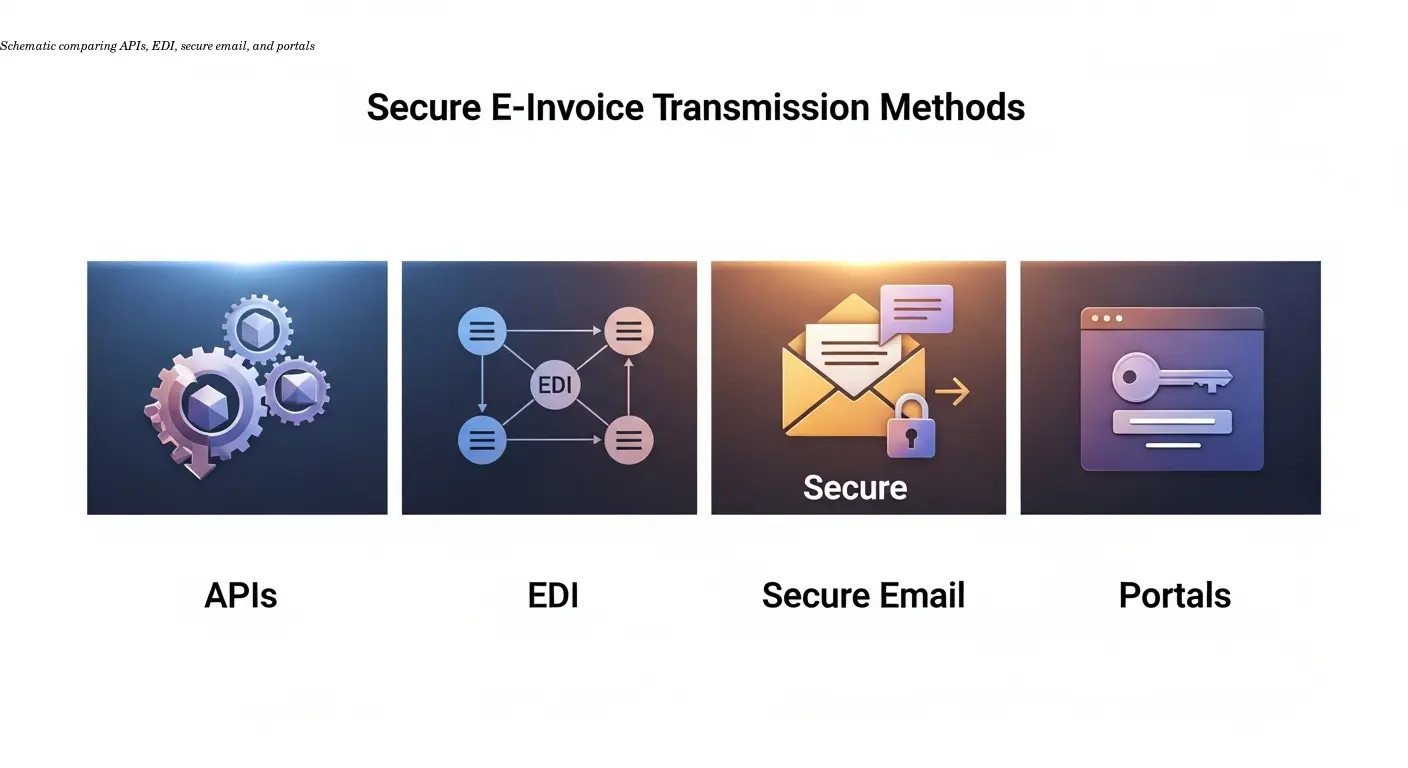
Choice of transport depends on volume, ERP integration, and regulatory needs. All methods must address encryption and partner authentication.
Encrypted web portals and APIs (TLS/HTTPS)
Common for cloud e-invoicing platforms exchanging XML, UBL, or JSON over TLS 1.2+/1.3. Often combined with mutual TLS (mTLS) for strong partner authentication. Verify platform certificate management, key storage, and access logging.
EDI and cXML networks
High-volume enterprises use EDI (EDIFACT, ANSI X12) via VANs or hubs. Encryption is typically transport-layer and sometimes payload signing. Setup overhead is higher but robust for established trading-partner agreements.
Secure email (S/MIME or PGP)
S/MIME adds encryption and signatures to emails but relies on mail routing and mailbox security—less robust for audit trails and non-repudiation compared with dedicated e-invoicing networks.
Portal upload and download
Suppliers upload invoices to a secure portal and buyers retrieve them over HTTPS. Requires strong authentication (MFA), session management, and secure portal development to avoid vulnerabilities (SQLi, XSS).
Real incident: a finance team that used email paid €80k to an attacker who intercepted supplier invoices and modified PDFs. They migrated to a secure API solution within two months.
Encryption Layers in Invoice Transmission
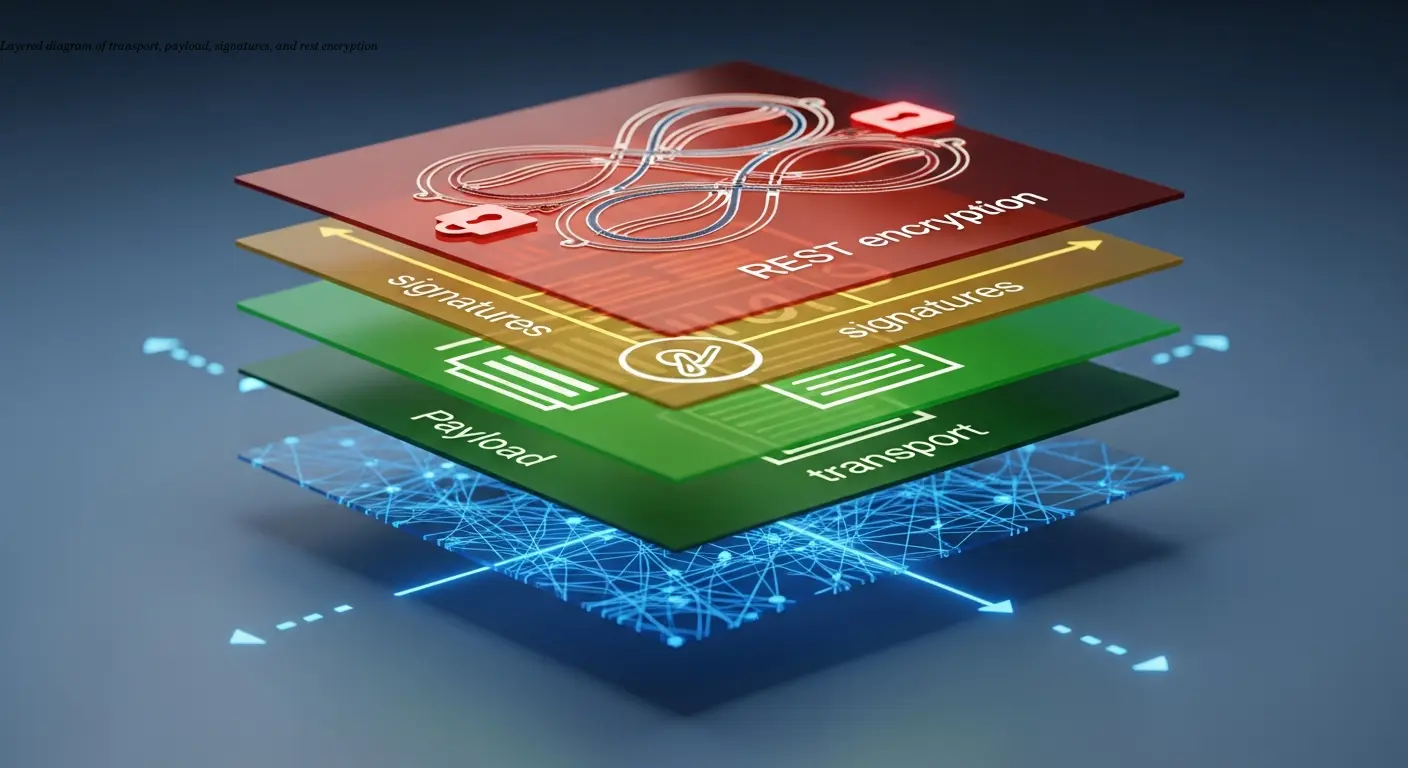
Secure setups typically combine multiple layers:
- Transport encryption (TLS) is the minimum baseline (TLS 1.2/1.3, strong ciphers, strict certificate validation).
- Content/payload encryption (public-key + symmetric hybrid) so only the intended recipient can decrypt—useful in multi-intermediary or cross-border cases.
- Digital signatures and seals (XMLDSig, PAdES, eIDAS qualified signatures) prove integrity and origin and, with timestamping, establish when the invoice existed in a particular form.
- Encryption at rest protects stored invoices, backups, and archives (server-side encryption, KMS-managed keys, role separation).
Operational example: excellent TLS and signing in transit were undone by plaintext storage in S3. Enabling server-side encryption with managed keys closed the gap.
Security Features in Modern E-Invoicing Platforms
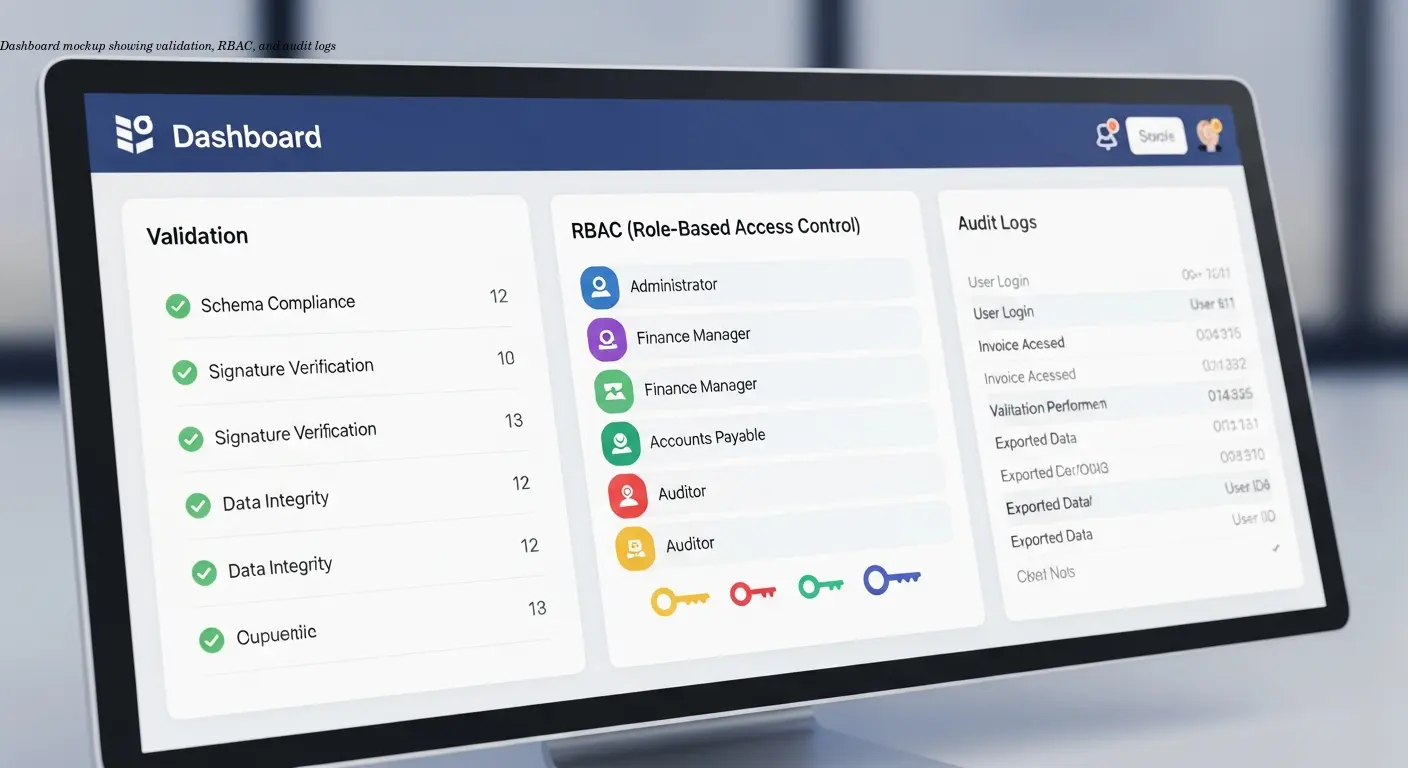
Modern platforms layer functionality around encrypted transmission to reduce external threats and operational risk:
- Role-based access control (RBAC) enforces segregation of duties and limits who can view, edit, approve, or delete invoices.
- Automated validation and fraud checks (PO matching, duplicate detection, anomaly detection) reduce manual error and prevent altered-payment scams.
- Unique identifiers and traceability give every invoice a global ID and detailed logs for audit reconstruction.
- Secure cloud infrastructure with certifications (ISO 27001, SOC 2), backups, and DR capabilities—balanced against vendor lock-in and data sovereignty considerations.
Operational tip: duplicate-detection features are sometimes off by default—ensure security-relevant defaults are enabled during setup.
Typical Secure Delivery Flows
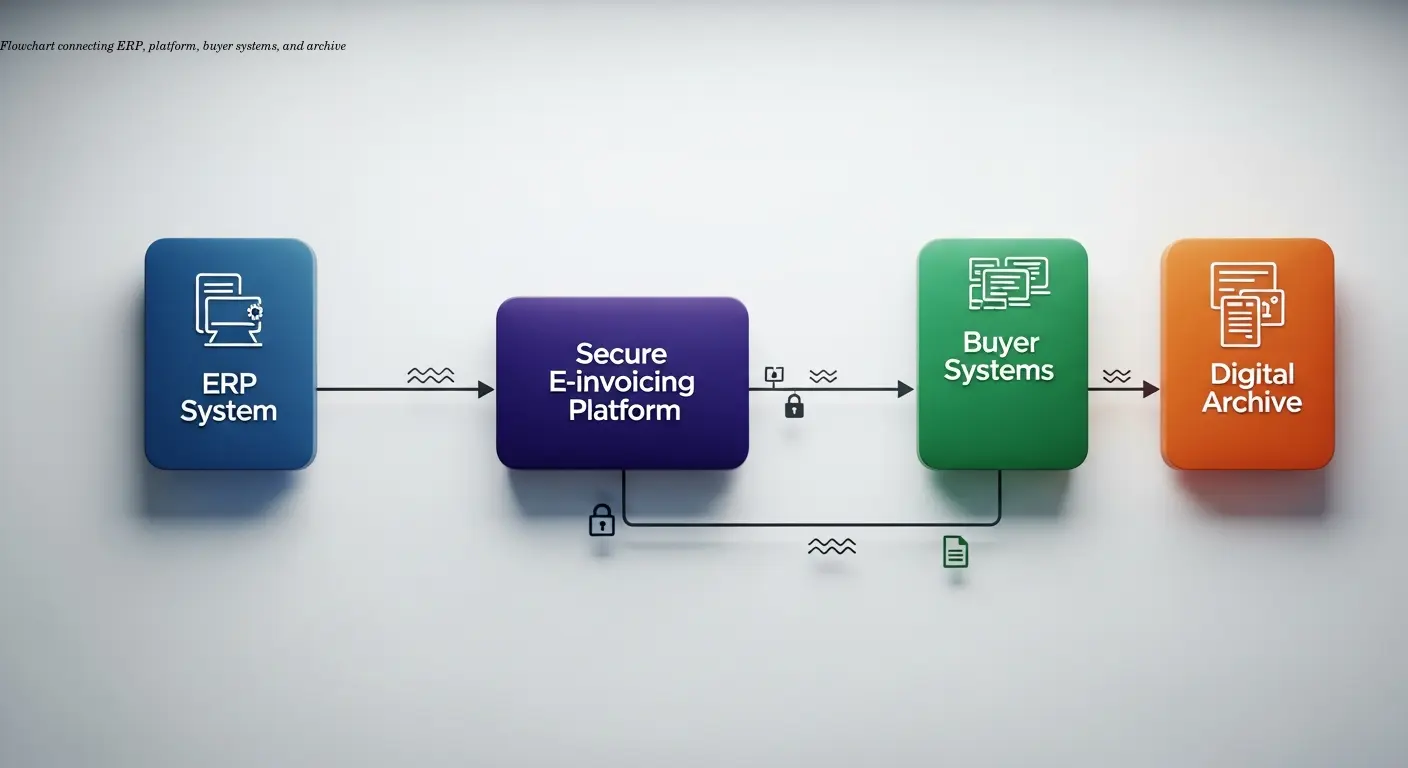
- Invoice generation: ERP creates a structured invoice (XML UBL/CII, ZUGFeRD, JSON) and optionally applies a digital signature after internal validation.
- Transfer to platform: Signed invoice moves to the e-invoicing platform over TLS APIs or secure file transfer (SFTP/FTPS); authenticate systems with API keys, OAuth tokens, or client certs.
- Platform processing: Validation, normalization (e.g., PEPPOL BIS conversion), and routing to the buyer via the agreed secure protocol (EDI, PEPPOL, API, portal).
- Buyer receipt: Buyer verifies signatures, performs PO matching, and routes exceptions to human reviewers.
- Archiving: Both parties store invoices plus signatures, timestamps, and logs in secure, audit-proof archives for the legally required retention period.
The principle: apply encryption, authentication, and logging at every handoff. Skip a link and that's where breaches occur.
Benefits of Secure and Encrypted E-Invoices
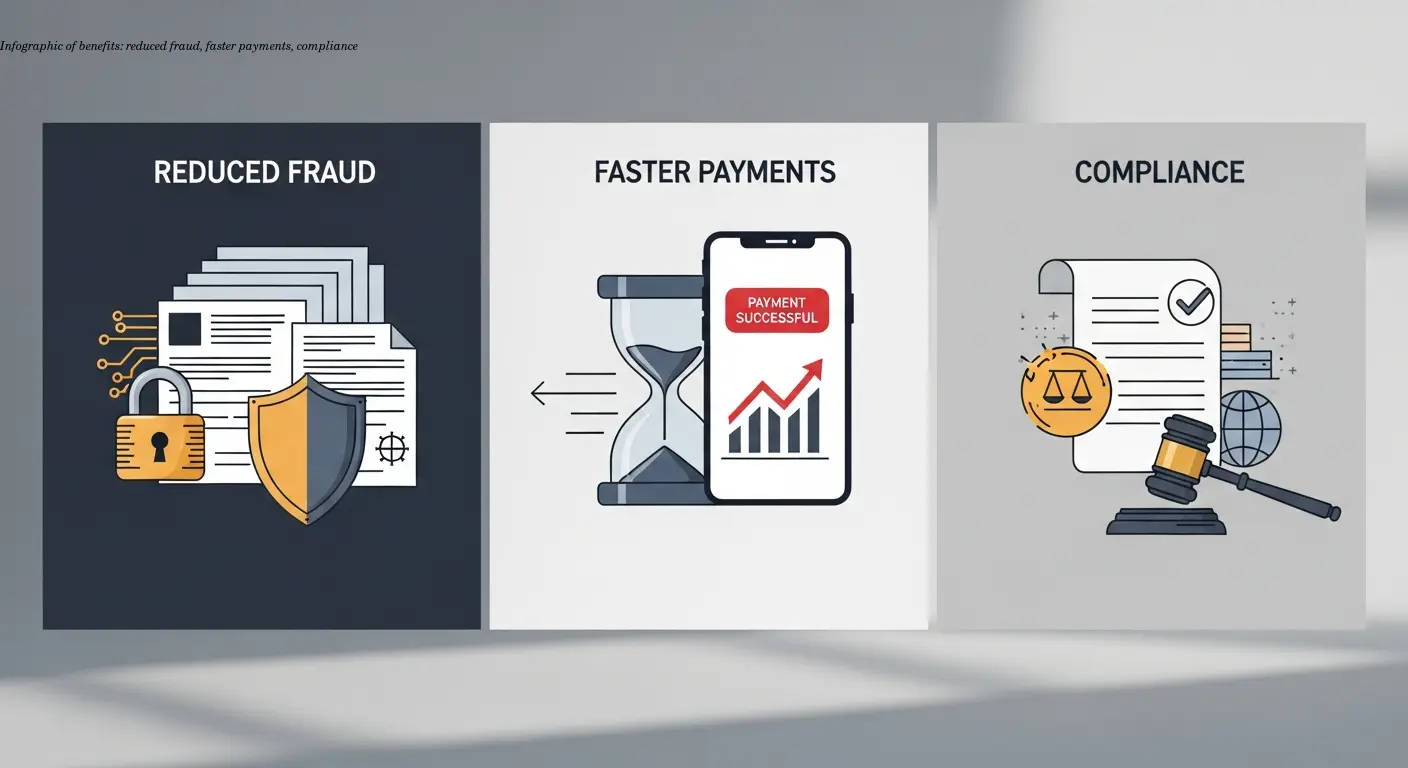
- Reduced fraud risk via signatures, encryption, and automated validation—making spoofing and payment diversion far harder.
- Stronger data protection to support GDPR and sector-specific confidentiality needs (healthcare, defense).
- Reliability and speed—real-time delivery confirmations and automated processing accelerate cash flow and supplier payments.
- Compliance and audit readiness—signatures, logs, and compliant archiving turn audits into evidence reviews instead of ad-hoc hunts.
From an IT security perspective: secure e-invoicing gives visibility into in-flight invoices, access events, and validation failures—something email-based workflows typically lack.
Practical Design Guidelines for IT and Security Teams

- Enforce strong, current transport encryption: TLS 1.2/1.3 only; disable legacy protocols and weak ciphers; automate certificate renewal and consider pinning for critical partners.
- Use payload-level protection where risk is high: payload encryption and qualified signatures for regulated or cross-border invoices—accept the key-management complexity for high-value protection.
- Implement robust identity and access management: MFA for portals, OAuth/API tokens with short TTLs, client certs for high-trust partners, RBAC, and regular access reviews.
- Automate validation and monitoring: schema checks, tax-ID verification, duplicate detection, anomaly alerts, and integration with SIEM/incident response workflows.
- Ensure compliant, secure archiving: retain invoices, signatures, timestamps, and logs for the legally required period with integrity checks and DR drills to validate restores.
Operational tip: run DR drills that restore invoice data and decryption keys to verify you can produce readable, verifiable invoices during audits. Keys on decommissioned HSMs lead to compliance failures.
FAQ
What is the difference between a secure e-invoice and a regular electronic invoice?
A regular electronic invoice is simply any invoice in digital form (PDF, XML, email attachment), while a secure e-invoice adds technical and process controls—encryption, digital signatures, access control, audit logging—to ensure confidentiality, integrity, authenticity, and non-repudiation. The difference is like sending a postcard versus a sealed registered letter with a signature-on-delivery requirement.
Do I need to encrypt the invoice content itself, or is TLS enough?
For most business-to-business invoicing, TLS (transport encryption) is enough if both endpoints and any intermediary platforms are trusted and properly secured. Content encryption (payload-level encryption) is recommended when invoices contain highly sensitive data, cross untrusted networks, or must meet strict regulatory confidentiality rules (e.g., healthcare, government contracts). It adds complexity, so evaluate your risk profile first.
What formats support digital signatures for e-invoices?
Standard structured formats like UBL, UN/CEFACT CII (used in ZUGFeRD, Factur-X), and PEPPOL BIS all support embedded XML digital signatures (XMLDSig). PDF invoices can carry signatures via PDF signing standards (PAdES). Many platforms also support detached signatures (a separate .sig or .p7s file) that travel alongside the invoice. The key is ensuring the signature covers the invoice data completely and uses a certificate chain that recipients can validate.
How do I verify the authenticity of an incoming e-invoice?
Check the digital signature against a trusted certificate (usually issued by a recognized CA or national trust service provider). Validate that the certificate hasn't been revoked (via CRL or OCSP). Cross-check the sender identifier in the invoice (tax ID, PEPPOL participant ID) against your supplier master data. Many platforms automate this verification and flag invoices that fail signature or sender checks.
Can secure e-invoicing prevent all invoice fraud?
No single technology prevents all fraud, but secure e-invoicing dramatically reduces common attack vectors—spoofed suppliers, altered bank details, duplicate invoices—by combining encryption, signatures, automated validation, and audit trails. Fraud that does occur (e.g., a compromised supplier account creating legitimate-looking fake invoices) is detected faster and with clearer evidence for investigation.
Are there EU-wide standards for secure e-invoice transmission?
The EU PEPPOL framework defines secure transmission standards (AS4, START) and invoice formats (PEPPOL BIS based on UBL or CII) used across member states. Germany mandates XRechnung or ZUGFeRD for B2G invoicing, France uses Chorus and Factur-X, Italy has FatturaPA—all with security requirements around signatures and encryption. eIDAS regulation provides the legal foundation for qualified electronic signatures and seals across the EU.
What are the retention and archiving requirements for secure e-invoices?
Most EU countries require invoice retention for 7–10 years, with requirements that invoices remain readable, authentic, and complete. This means secure archiving must preserve not just the invoice file but also signatures, timestamps, and metadata. Long-term signature validation (LTV) techniques are often needed to ensure signatures remain verifiable even after the original certificates expire.
How can I create EU-compliant e-invoices with built-in security?
Platforms like e-rechn.de generate structured e-invoices in compliant formats (XRechnung, ZUGFeRD) with options for digital signatures and encrypted delivery, handling the technical complexity so you can focus on your invoicing workflow. Such tools integrate validation, secure transmission, and archiving features aligned with EU regulations, reducing the risk of non-compliance or security gaps.
